Google Chrome: As of Chrome 49, the keygen function has been disabled by default and digital certificate file types are downloaded instead of installed. While the keygen function can manually be enabled, the custom filetype handling is still removed, therefore installation through Google Chrome is not supported. Some features of Chromium use Google APIs, and to access those APIs, either an API Key or a set of OAuth 2.0 tokens is required. Setting up API keys is optional. If you don't do it, the specific APIs using Google services won't work in your custom build, but all other features will run normally. Google Chrome: As of Chrome 49, the keygen function has been disabled by default and digital certificate file types are downloaded instead of installed. While the keygen function can manually be enabled, the custom filetype handling is still removed, therefore installation through Google Chrome.
New Users: Before you can start using the Google Maps Platform APIs and SDKs, you must sign up and create a billing account.To learn more, see Get Started with Google Maps Platform.
Securely access your computer from your phone, tablet, or another computer. It's fast, simple, and free. 1.1 Your use of Google’s products, software, services and websites (referred to collectively as the “Services” in this document and excluding any services provided to you by Google under a separate written agreement) is subject to the terms of a legal agreement between you and Google. Meet True Key™ by McAfee – the easier, safer way to unlock your digital world. No more hassle of remembering multiple passwords – conveniently log in to your apps, sites and devices with the True Key app. Quick and Simple Access From the moment you open your browser, the True Key browser extension helps you access your accounts easily.
To use the Maps Embed API you must have an API key. The API key is a unique identifier that isused to authenticate requests associated with your project for usage and billing purposes.
Get the API key
You must have at least one API key associated with your project. Reimage license key generator 2014.
To get an API key:
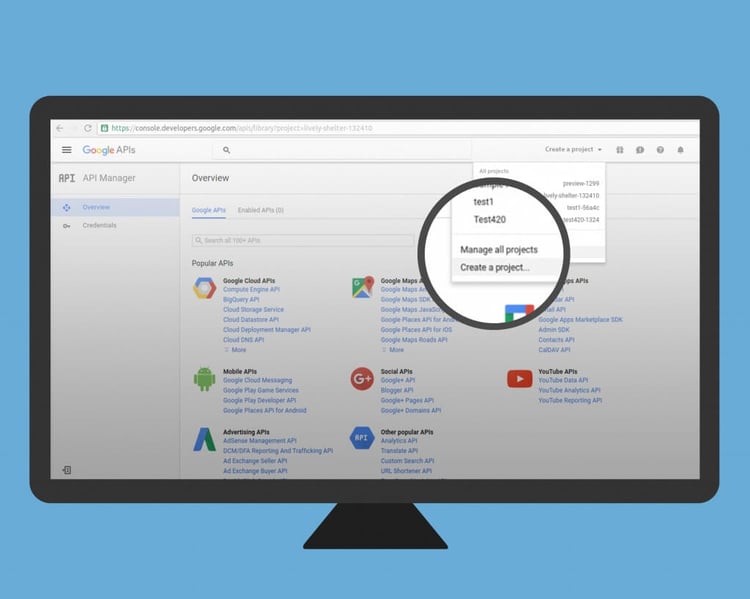
- Visit the Google Cloud Platform Console.
- Click the project drop-down and select or create the project for which you want to add an API key.
- Click the menu button and select APIs & Services > Credentials.
- On the Credentials page, click Create credentials > API key.
The API key created dialog displays your newly created API key. - Click Close.
The new API key is listed on the Credentials page under API keys.
(Remember to restrict the API key before using it in production.)
Add the API key to your request
You must include an API key with every Maps Embed API request.In the following example, replace YOUR_API_KEY withyour API key.
Allow Google Chrome
For more information about MODE and parameters options in the code above, see Forming the URL for the Maps Embed API.
Restrict the API key
We strongly recommend that you restrict your API key. Restrictions provide added security and helpensure only authorized requests are made with your API key. There are two restrictions. You shouldset both:
- Application restriction: Limits usage of the API key to either websites (HTTP referrers), web servers (IP addresses), or mobile apps (Android apps or iOS apps). You can select only one restriction from this category, based on the platform of the API or SDK (see GMP APIs by Platform).
Note: If you need to call web, web service, and/or mobile APIs from the same (client-side) app, create and restrict multiple keys.
- API restriction: Limits usage of the API key to one or more APIs or SDKs. Requests to an API or SDK associated with the API key will be processed. Requests to an API or SDK not associated with the API key will fail. (The API or SDK must be enabled and must support the application restriction.)
To restrict an API key:
- Go to the Google Cloud Platform Console.
- Click the project drop-down select the project that contains the API key you want to secure.
- Click the menu button and select APIs & Services > Credentials.
- On the Credentials page, click the name of the API key that you want to secure.
- On the Restrict and rename API key page, set the restrictions:
- Application restrictions
- Select HTTP referrers (web sites).
- Add the referrers.
- API restrictions
- Select Restrict key.
- Click Select APIs and select Maps Embed API.
(If the Maps Embed API is not listed, you need to enable it.)
- Click SAVE.
Google Chrome Keys Not Working
For Developers > Design Documents > Password GenerationOverview
Passwords are not a very good form of authentication. They are easy to use but they are trivial to steal, either through phishing, malware, or a malicious/incompetent site owner. Furthermore, since people are so apt to reuse passwords losing one password leaks a substantial amount of your internet identity. Chrome's long term solution to this problem is browser sign in plus OpenID. While implementing browser sign in is something that we can control, getting most sites on the internet to use OpenID will take a while. In the meantime it would be nice to have a way to achieve thesame affect of having the browser control authentication. Currently you can mostly achieve this goal through Password Manager and Browser Sync, but users still know their passwords so they are still susceptible to phishing. By having Chrome generate passwords for users, we can remove this problem. In addition to removing the threat of phishing, automatically generating password is a good way to promote password manager use, which should be more secure and seamless than manual password management. Design Generating and Updating Passwords Detecting when we are on a page that is meant for account sign up will be most of the technical challenge. This will be accomplished by a combination of local heuristics and integration with Autofill. In particular, the password manager will upload information to Autofill servers when a user signs in using a saved password on a form different from the one it was saved on. This gives a strong signal that the original form was used for account creation. This data is then aggregated to determine if the form is or isn't used for account creation. Those that are will be labeled as such by Autofill. If a signal is received from Autofill when the form is rendered, we mark the password field. When the users focuses this field, we show an Autofill like dropdown with a password suggestion.
The generated password is generic enough that it works on most sites as is, but not all sites have the same requirements. Eventually we will use additional signals to craft the generated password we use, but for now we ease editing by showing the password if the user focuses the field and also sync any changes made to the confirm password field (if one exists).
The user doesn't need to explicitly save a password that is generated as it happens automatically, and they should go through the normal password management experience from that point on. Retrieving Passwords While generally it's good that users don't know their passwords, there are times when they will need them such as when they aren't able to use Chrome. For these cases, we will have a secure password storage web site where users can sign in and view (and possibly export?) their passwords. Since it should be relatively rare that users need this, and since this information is valuable, we are debating adding additional safety checks here, such as a prompt to enable StrongAuth. TODO(gcasto): Add link once this site is live.
PasswordGenerationAgentis responsible for both detecting account creation password fields and properly filling and updating the passwords depending on the users interaction with the UI. Browser PasswordGenerationManager takes messages from the renderer and makes an OS specific dropdown. This UI use a PasswordGenerator to create a reasonable password for this site (tries to take in account maxlength attribute, pattern attribute, etc.). If the password is accepted, it is sent back to the renderer. Caveats Users must have password sync enabled Since users are not going to know their passwords, we need to be able to retrieve it for them no matter which computer they are using. Not all websites can be protected This feature only works for sites that work with both the password manager and Autofill. Currently this means sites that do signup with only two input fields (e.g. Netflix) aren't covered since Autofill doesn't upload in this case. It also means that sites that don't work with the password manager (e.g. sites that login without navigation) aren't covered. Users are only protected for new passwords We will not force users to use this feature, we simply suggest it when they sign up. Eventually we will want to prompt on change password forms as well, though the password manager currently doesn't have this capability. Feature makes Google a higher value hijacking target Google is already a high value target so this shouldn't changes much. Moreover it's easier for us to make logging into Google more secure via StrongAUTH than have every site on the internet secure itself. At some point in the future it might also be possible for us to automatically change all of a users passwords when we realize that their account is hijacked. |
|

