Generate A Ssh Key On Mac For Github
Create SSH key. Contribute to s3p02/createsshmacandlinuxandwindows development by creating an account on GitHub. If you don't have an existing public and private key pair, or don't wish to use any that are available to connect to GitHub, then generate a new SSH key. If you see an existing public and private key pair listed (for example idrsa.pub and idrsa) that you would like to use to connect to GitHub, you can add your SSH key to the ssh-agent.
Creating a SSH Public Key on OSX; Edit on GitHub View source. To generate SSH keys in Mac OS X, follow these steps: Enter the following command in the Terminal window: ssh-keygen -t rsa -b 4096. This starts the key generation process. When you execute this command, the ssh-keygen utility prompts you to indicate where to store the key. Creating Keys. This is a brief guide to creating a public/private key pair that can be used for OpenSSL. While the 'easy' version will work, I find it convenient to generate a single PEM bundle and then export the private/public key from that as needed.

- Generate & Load Keys
- Setup the Proxy (Show me the magic!)
Overview
There are often times when you cannot SSH directly to a system, perhaps its behind a firewall or a NAT. SSH has an ability to proxy commands through other SSH systems. We’ll call this the jump box. For systems using OpenSSH, you could feasibly hop through several systems, but we’ll focus on just a single hop.
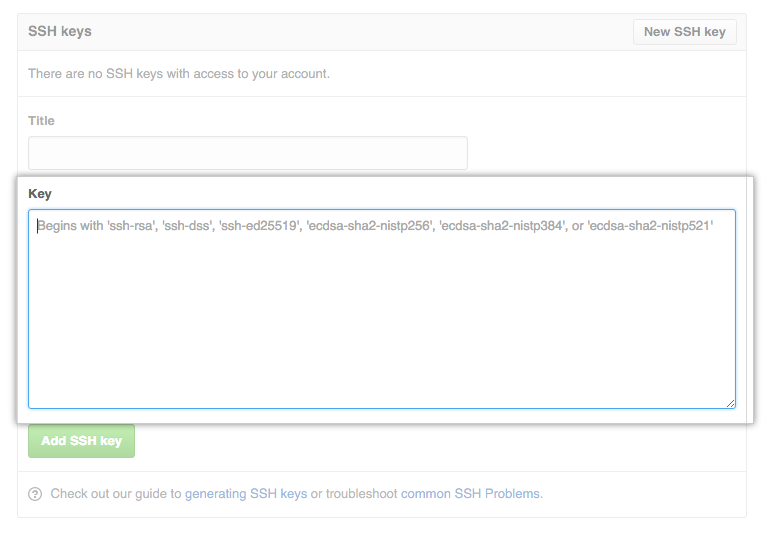
Generate & Load Keys
First things first, you’re going to need some crypto keys.
OpenSSH (Linux or Mac)
If you do not already have RSA (or EC) keys, you can generate the default key path using the following command in a terminal.
This will store the key in ${HOME}/.ssh/id_rsa by default and prompt you for a passphrase. On both a Mac and Linux graphical desktops, this passphrase can be managed by the desktop keyring, so go ahead and make it a strong one. Either way, you only have to enter it once per user session.
Your public key is stored in ${HOME}/.ssh/id_rsa.pub. This is the file that you will need to copy to remote systems, and as the name implies, is safe to freely share to authenticate yourself.
Finally, you want to load it into your SSH key agent. First, test that you have an SSH agent loaded by trying to list your current keys.
If this states that you cannot connect to an agent, we’ll need to start one.
Now add your key (it will prompt you for your key passphrase)
You should now be able to view your identity
Putty Key Generation
/generate-key-file-existing-database.html. Sourced from link::https://www.digitalocean.com/community/tutorials/how-to-create-ssh-keys-with-putty-to-connect-to-a-vps[Digital Ocean]
While PuTTY is a client program for SSH (in addition to Telnet and Rlogin), it is not a port of or otherwise based on OpenSSH. Consequently, PuTTY does not have native support for reading OpenSSH’s SSH-2 private key files. However, PuTTY does have a companion named PuTTYgen (an RSA and DSA key generation utility), that can convert OpenSSH private key files into PuTTY’s format; allowing you to connect to your cloud server from a Windows machine, with the added security that SSH keys provide.
PuTTYgen is a (free) open-source utility and can be downloaded from the maintainer’s website. PuTTYgen is what you will use to generate your SSH keys for use in PuTTY. To start, all you need to do is download the exectuable files (.exe) and save them on the computer that you’ll use to connect to your VPS, e.g. on the desktop. You will not need to 'install' PuTTYgen, because it is a standalone application.
Generating OpenSSH-compatible Keys for Use with PuTTY
Start the PuTTYgen utility, by double-clicking on its .exe file;
For Type of key to generate, select SSH-2 RSA;
In the Number of bits in a generated key field, specify either 2048 or 4096 (increasing the bits makes it harder to crack the key by brute-force methods);
Click the Generate button;
Move your mouse pointer around in the blank area of the Key section, below the progress bar (to generate some randomness) until the progress bar is full;
A private/public key pair has now been generated;
In the Key comment field, enter any comment you’d like, to help you identify this key pair, later (e.g. your e-mail address; home; office; etc.) — the key comment is particularly useful in the event you end up creating more than one key pair;
You should type a passphrase in the Key passphrase field & re-type the same passphrase in the Confirm passphrase field. Since we’ll be using an agent to load the keys, you’ll only have to type this once per session. Make it a strong passphrase.
Click the Save public key button & choose whatever filename you’d like (some users create a folder in their computer named my_keys);
Click the Save private key button & choose whatever filename you’d like (you can save it in the same location as the public key, but it should be a location that only you can access and that you will NOT lose! If you lose your keys and have disabled username/password logins, you will no longer be able log in!);
Right-click in the text field labeled Public key for pasting into OpenSSH authorized_keys file and choose Select All;
Right-click again in the same text field and choose Copy. Use this to setup the Public Key on the Remote Server(s) after we setup your ssh agent using Pageant.
Add Your Key to Pageant
Sourced from link::https://www.digitalocean.com/community/tutorials/how-to-use-pageant-to-streamline-ssh-key-authentication-with-putty[Digital Ocean]
If you installed the full distribution of PuTTY, you will have a number of utilities in the same directory as putty.exe. Namely, pageant.exe, plink.exe, and others. Launch Pageant. It will start minimized to the system tray by default. Right-click on the icon and select View Keys.
Click the Add Key button. This will open the file explorer, wher eyou can choose one or more keys at a time to load. You should select files with .ppk extension, which is the PuTTY key format.
If the key is passphrase-protected, Pageant will ask for your passphrase for that key. Once your key is loaded, you will no longer be prompted for the passphrase.
Once successfully loaded, you will see it listed in the Pageant Key List window.
Setup Your Public Key on the Remote Server(s)
Now it’s time to setup the remote server. You will want to do this on the jump box and the final endpoint.
SSH to the system and ensure your
.sshis set up. SSH requires read and write privileges to only your user account. Without this, it will fail.
Now add your public key to the file ${HOME}/.ssh/authorized_keys. This is from id_rsa.pub on your local system (or the key we copied from PuTTY).
Generate A Ssh Key On Mac For Github Pc
After you’ve done this on the jump box, try logging in again. If everything is setup correctly, you shouldn’t be prompted for a password.
From the jumpbox, ssh to your next hop and repeat the process. To test your keys on the next hop, connect to the jumpbox with the option to Forward SSH Agent. This is ssh -A user@jumpbox using OpenSSH. It is in the SSH options in PuTTY.
Setup the Proxy (Show me the magic!)
OpenSSH
On your local workstation, edit the file (or create if needed) ${HOME}/.ssh/config. This file lets us set per-host preferences for SSH.
This is the hostname, IP address, or alias that SSH will match on
The
Useroption is only needed if it differs from your local usernameThis is the hostname that SSH will actually try to connect to. It can be a DNS resolvable name or an IP address
This tells SSH to forward your agent socket to the remote systems so you can authenticate to other systems
This is what tells SSH how to connect to this system through another system. In this case, we use the alias
jumpboxwhich is also defined in this file.
You should now be able to SSH directly to your endpoint! Try it out!
PuTTY
Sourced from link::https://monkeyswithbuttons.wordpress.com/2010/10/01/ssh-proxycommand-and-putty/[Monkeys With Buttons] blog
The concepts of the PuTTY configuration are similar. Create a connection entry as normal (specifying username in Data if needed), and select Connection → Proxy.
Specify the proxy type as local and put the jumpbox hostname as the Proxy Hostname. The equivalent to the ProxyCommand in OpenSSH is the lower box labelled Telnet command, or local proxy command. Enter the following:
Your configuration should look something like this:
Generate A Ssh Key On Mac For Github Free
Thats it! Get back to work!
This version of GitHub Enterprise will be discontinued on This version of GitHub Enterprise was discontinued on 2019-10-16. No patch releases will be made, even for critical security issues. For better performance, improved security, and new features, upgrade to the latest version of GitHub Enterprise.For help with the upgrade, contact GitHub Enterprise support.
Before you generate an SSH key, you can check to see if you have any existing SSH keys.
Note: DSA keys were deprecated in OpenSSH 7.0. If your operating system uses OpenSSH, you'll need to use an alternate type of key when setting up SSH, such as an RSA key. For instance, if your operating system is MacOS Sierra, you can set up SSH using an RSA key.
Open TerminalTerminalGit Bashthe terminal.
Enter
ls -al ~/.sshto see if existing SSH keys are present:Check the directory listing to see if you already have a public SSH key.
By default, the filenames of the public keys are one of the following:
- id_dsa.pub
- id_ecdsa.pub
- id_ed25519.pub
- id_rsa.pub
- If you don't have an existing public and private key pair, or don't wish to use any that are available to connect to GitHub, then generate a new SSH key.
- If you see an existing public and private key pair listed (for example id_rsa.pub and id_rsa) that you would like to use to connect to GitHub, you can add your SSH key to the ssh-agent.
Tip: If you receive an error that ~/.ssh doesn't exist, don't worry! We'll create it when we generate a new SSH key.